Wednesday, 19 October 2016
Tuesday, 18 October 2016
Q:How to write a resume with no job experience?
QUICK ANSWER:
To write a resume with no job experience, make an informative list, review sample resumes, and utilize available templates. Take steps to ensure your resume is formatted properly, and review all the information for accuracy. Do not include references on your resume. Make a separate reference page.
keep learning
Full Answer:
Compile a List
Compile a list of information to use for your resume. This list should include the basics, such as your name and address. It should also include your skills, related coursework and any volunteer work or awards.Review sample resumes
Review sample resumes with no work experience to help you get an idea of how yours should look.
Utilize resume templates
Using one of the resume templates available with Microsoft Word, enter the information from your list.
Ensure proper formation
Once you have added all of your information into the template, ensure proper formation. Keep the wording simple and easy to understand, and use a plain font to ensure your resume is easy to read.
Review your resume
Review your finished resume for accuracy, and have a friend or family member proofread it for accuracy.
Make a reference page
Create a separate reference page. Since you do not have professional work references, list teachers, coaches, neighbors, or family friends who can vouch for your character and ethics.
Thursday, 13 October 2016
Thursday, 6 October 2016
HOW TO GET A JOB (VERY EASY STEP).
Students: Applying to Google
- An updated resume
- A transcript from your university (unofficial is fine)
- In some cases, a cover letter, short essay, or additional information listed in the job description
Focus on your resume
Your resume is the first piece of information we’ll see about you. Here’s how to highlight your achievements:
- Align your skills and experience with the internship or job description
- Be specific about projects you’ve worked on or managed. What was the outcome? How did you measure success?
- If you've had a leadership role in a volunteer organization or at a part-time job, tell us about it. How big was the team? What was the scope of your work?
- Include your GPA, as well as school-related projects or coursework that demonstrate relevant skills and knowledge
- Keep it short: Aim for one page. If there’s additional information we need during the hiring process, (like a portfolio), your recruiter will work with you to collect it
Prepare for the interview process
- Once you’ve submitted your application online, our staffing team will review your resume, transcript, and any supplementary materials
- The next step in the process is a series of interviews—which may be on the phone, via video conference, or in person—to assess your skills
- For technical interviews, practice coding on a whiteboard, in Google Docs, or over the phone. You can find sample coding questions on sites like LeetCode, CodeLab, Quora, and Stack Overflow. The book “Cracking the Coding Interview” is also a good resource
- Structure your interview answers: It’s important to show how you arrive at a solution, so think out loud
Helpful questions to think about as you prepare:
- How do you work best, both as an individual and as part of a team?
- What challenges have you faced at school or at work and how did you overcome them?
- Which of your skills or experiences would be assets in the role and why?
If you don’t understand a question, ask your interviewers for clarification and take the time you need with responses.
Watch :Technical Interview Tips Click here
Wednesday, 5 October 2016
Define the Turing test and its significance.
A Turing test is a test performed to determine a machine’s ability to exhibit intelligent behavior. The basic concept behind the test is that if a human judge is engaged in a natural language conversation with a computer where he cannot reliably distinguish machine from human, the machine passes the test. Responses from both participants in the conversation are received in the form of a text-only channel. This test was introduced by Alan Turing in 1950.
The Turing test is used to measure a machine's ability to think and is an important concept in the philosophy of artificial intelligence. A machine’s success at thinking can be quantified by the likelihood that a human will misidentify it as a human subject.
A computer's ability to think is determined through an imitation game. In this game, there are three players A, B and C. Player A is a man, B a woman and C is of either sex. C cannot see A and B, and communicates with the others through written notes. Player C determines which of the others is a man and which is a woman by asking a series of questions. Player A tricks the interrogator into making the wrong decision, while B attempts to guide C toward the right path.
In the original imitation game test, Turing proposes A to be a computer. The computer pretends to be a woman and tricks the interrogator into making an incorrect evaluation. The machine's success is determined by comparing the outcome of the game when A is a computer against when A is a man. If the interrogator goes wrong when playing the game between man and woman, the computer is assessed to be intelligent.
There are some variations on the interpretation of how a Turing test should be performed but the basic premise is whether a human judge can determine whether he is talking to a machine or another human.
if you wan a watch the vedio of Turing Test Then Please Click here
The Turing test is used to measure a machine's ability to think and is an important concept in the philosophy of artificial intelligence. A machine’s success at thinking can be quantified by the likelihood that a human will misidentify it as a human subject.
A computer's ability to think is determined through an imitation game. In this game, there are three players A, B and C. Player A is a man, B a woman and C is of either sex. C cannot see A and B, and communicates with the others through written notes. Player C determines which of the others is a man and which is a woman by asking a series of questions. Player A tricks the interrogator into making the wrong decision, while B attempts to guide C toward the right path.
In the original imitation game test, Turing proposes A to be a computer. The computer pretends to be a woman and tricks the interrogator into making an incorrect evaluation. The machine's success is determined by comparing the outcome of the game when A is a computer against when A is a man. If the interrogator goes wrong when playing the game between man and woman, the computer is assessed to be intelligent.
There are some variations on the interpretation of how a Turing test should be performed but the basic premise is whether a human judge can determine whether he is talking to a machine or another human.
if you wan a watch the vedio of Turing Test Then Please Click here
Define Artificial Intelligence in detail with the application areas.
Artificial intelligence (AI) is an area of computer science that emphasizes the creation of intelligent machines that work and react like humans.
Some of the activities computers with artificial intelligence are designed for include:
Some of the activities computers with artificial intelligence are designed for include:
- Speech recognition
- Learning
- Planning
- Problem solving
Research associated with artificial intelligence is highly technical and specialized. The core problems of artificial intelligence include programming computers for certain traits such as: Knowledge
aspects of the world, while computer vision is the power to analyze visual inputs with few sub-problems such as facial, object and speech recognition. Robotics is also a major field related to AI. Robots require intelligence to handle tasks such as object manipulation and navigation, along with sub-problems of localization, motion planning and mapping.
Applications of Artificial Intelligence:-
- Reasoning
- Problem solving
- Perception
- Learning
- Planning
- Ability to manipulate and move objects
Knowledge engineering is a core part of AI research. Machines can often act and react like humans only if they have abundant information relating to the world. Artificial intelligence must have access to objects, categories, properties and relations between all of them to implement knowledge engineering. Initiating common sense, reasoning and problem-solving power in machines is a difficult and tedious approach.
Machine learning is another core part of AI. Learning without any kind of supervision requires an ability to identify patterns in streams of inputs, whereas learning with adequate supervision involves classification and numerical regressions. Classification determines the category an object belongs to and regression deals with obtaining a set of numerical input or output examples, thereby discovering functions enabling the generation of suitable outputs from respective inputs. Mathematical analysis of machine learning algorithms and their performance is a well-defined branch of theoretical computer science often referred to as computational learning theory.
Machine perception deals with the capability to use sensory inputs to deduce the different
aspects of the world, while computer vision is the power to analyze visual inputs with few sub-problems such as facial, object and speech recognition. Robotics is also a major field related to AI. Robots require intelligence to handle tasks such as object manipulation and navigation, along with sub-problems of localization, motion planning and mapping.
Applications of Artificial Intelligence:-
- Problem Solving
- Game Playing
- Theorem Proving
- Natural Language Processing & Understanding
- Perception General(Speech Reorganization · Pattern Reorganization)
- Image Processing
- Expert System
- Computer Vision
- Robotics
- Intelligent Computer Assisted Instruction
- Automatic programming
- Planning & Decision Support systems
- Engineering Design & Comical Analysis
- Neural Architecture.
- Heuristic Classification.
Monday, 3 October 2016
Q. Explain the concept of Class and objects. How can constructors be used in JAVA explain with a program?
Answer(its Vedio Lecture in your language)
class classname
{
Field declarations;
Methods declarations:
}
A class can contain any of the following variable types.
1.Local variables: Variables defined inside methods, constructors or blocks are called local variables. The variable will be declared and initialized within the method and the variable will be destroyed when the method has completed.
2.Instance variables: Instance variables are variables within a class but outside any method. These variables are instantiated when the class is loaded. Instance variables can be accessed from inside any method, constructor or blocks of that particular class.
3.Class variables: Class variables are variables declared with in a class, outside any method, with the static keyword. It can be tedious to initialize all of the variables in a class each time an instance is created. Because the requirement for initialization is so common, Java allows objects to initialize themselves when they are created. This automatic initialization is performed through the use of a constructor.
Creating and declaring objects;
Obtaining objects of a class in two steps
• Declare a variable of class type, it does not define an object, instead it is simply a variable that
can refer to an object. Rectangle rect1; // declare
• Declaration creates a physical copy of that object and assign it to that variable and returns
reference to it. rect1=new Rectangle(); // instantiation
Accessing class members
We can access the instance variables and the methods with the use of concerned objects and dot operator.
Obj.varaiable=value;
Obj.method(parameter list);
Constructors look a little strange because they have no return type, not even void. This is because the implicit return type of a class' constructor is the class type itself. It is the constructor's job to initialize the internal state of an object so that the code creating an instance will have a fully initialized, usable object immediately.
Example
class Box {
double width;
double height;
double depth;
// This is the constructor for Box.
Box() {
System.out.println("Constructing Box");
width = 10;
height = 10;
depth = 10;
}
// compute and return volume
double volume() {
return width * height * depth;
}
}
class BoxDemo
{
public static void main(String args[])
{
// declare, allocate, and initialize Box objects
Box mybox1 = new Box();
Box mybox2= new Box();
double vol; // get volume of first box
vol = mybox1.volume();
System.out.println("Volume is " + vol);
// get volume of second box
vol = mybox2.volume();
System.out.println("Volume is " + vol);
}
}
Class
Class is a collection of objects of same type. It provides a convenient way for packing together a group of related data items and functions. A class is declared by using a keyword class.class classname
{
Field declarations;
Methods declarations:
}
A class can contain any of the following variable types.
1.Local variables: Variables defined inside methods, constructors or blocks are called local variables. The variable will be declared and initialized within the method and the variable will be destroyed when the method has completed.
2.Instance variables: Instance variables are variables within a class but outside any method. These variables are instantiated when the class is loaded. Instance variables can be accessed from inside any method, constructor or blocks of that particular class.
3.Class variables: Class variables are variables declared with in a class, outside any method, with the static keyword. It can be tedious to initialize all of the variables in a class each time an instance is created. Because the requirement for initialization is so common, Java allows objects to initialize themselves when they are created. This automatic initialization is performed through the use of a constructor.
Creating and declaring objects;
Obtaining objects of a class in two steps
• Declare a variable of class type, it does not define an object, instead it is simply a variable that
can refer to an object. Rectangle rect1; // declare
• Declaration creates a physical copy of that object and assign it to that variable and returns
reference to it. rect1=new Rectangle(); // instantiation
Accessing class members
We can access the instance variables and the methods with the use of concerned objects and dot operator.
Obj.varaiable=value;
Obj.method(parameter list);
Constructors
A constructor initializes an object immediately upon creation. It has the same name as the class in which it resides and is syntactically similar to a method. Once defined, the constructor is automatically called immediately after the object is created, before the new operator completes.Constructors look a little strange because they have no return type, not even void. This is because the implicit return type of a class' constructor is the class type itself. It is the constructor's job to initialize the internal state of an object so that the code creating an instance will have a fully initialized, usable object immediately.
Example
class Box {
double width;
double height;
double depth;
// This is the constructor for Box.
Box() {
System.out.println("Constructing Box");
width = 10;
height = 10;
depth = 10;
}
// compute and return volume
double volume() {
return width * height * depth;
}
}
class BoxDemo
{
public static void main(String args[])
{
// declare, allocate, and initialize Box objects
Box mybox1 = new Box();
Box mybox2= new Box();
double vol; // get volume of first box
vol = mybox1.volume();
System.out.println("Volume is " + vol);
// get volume of second box
vol = mybox2.volume();
System.out.println("Volume is " + vol);
}
}
Q. Explain different types of Selection Control statements in JAVA with syntax. Write a program in JAVA to find the greatest number among three given numbers. Your program should take input from the user.
Answer
Control Statements
The statements inside your source files are generally executed from top to bottom, in the order that they appear Control flow statements, however, break up the flow of execution by employing decision making, looping, and branching, enabling your program to conditionally execute particular blocks of code. ava contains the following types of control statements:
1- Selection Statements
2- Repetition Statements
3- Branching Statements
Selection statements
If Statement:
This is a control statement to execute a single statement or a block of code, when the given condition is true and if it is false then it skips if block and rest code of program is executed .
Syntax:
if(conditional_expression){
<statements>;
...;
...;
}
If-else Statement:
The "if-else" statement is an extension of if statement that provides another option when 'if' statement
evaluates to "false" i.e. else block is executed if "if" statement is false.
Syntax: if(conditional_expression){
<statements>;
...;
...; }
else{ <statements>;
....;
....;
}
Switch Statement:
This is an easier implementation to the if-else statements. The keyword "switch" is followed by an expression
that should evaluates to byte, short, char or int primitive data types ,only. In a switch block there can be one
or more labeled cases. The expression that creates labels for the case must be unique. The switch expression
is matched with each case label. Only the matched case is executed ,if no case matches then the default
statement (if present) is executed.
Syntax:
switch(control_expression){ case
expression 1: <statement>; case
expression 2: <statement>;
...
... case expression n:
<statement>; default:
<statement>;
}//end switch
Write a program in JAVA to find the greatest number among three given numbers. Your program should take input from the user
Answer.
import java.io.*;
class GreatestNumber
{
public static void main(String args[]) throws java.lang.Exception
{
int n1,n2,n3;
BufferedReader buffer = new BufferedReader (new InputStreamReader(System.in));
System.out.println("Enter First number");
n1=Integer.parseInt(buffer.readLine());
System.out.println("Enter Second number");
n2=Integer.parseInt(buffer.readLine());
System.out.println("Enter Third number");
n3=Integer.parseInt(buffer.readLine());
if(n1>n2)
{
if(n1>n3)
{
System.out.println("n1 = "+n1+" is greater");
}
else
{
System.out.println("n3 = "+n3+" is greater");
}
}
else
{
if(n2>n3)
{
System.out.println("n2 = "+n2+" is greater");
}
else
{
System.out.println("n3 = "+n3+" is greater");
}
}
}
}
sos
Control Statements
The statements inside your source files are generally executed from top to bottom, in the order that they appear Control flow statements, however, break up the flow of execution by employing decision making, looping, and branching, enabling your program to conditionally execute particular blocks of code. ava contains the following types of control statements:
1- Selection Statements
2- Repetition Statements
3- Branching Statements
Selection statements
If Statement:
This is a control statement to execute a single statement or a block of code, when the given condition is true and if it is false then it skips if block and rest code of program is executed .
Syntax:
if(conditional_expression){
<statements>;
...;
...;
}
If-else Statement:
The "if-else" statement is an extension of if statement that provides another option when 'if' statement
evaluates to "false" i.e. else block is executed if "if" statement is false.
Syntax: if(conditional_expression){
<statements>;
...;
...; }
else{ <statements>;
....;
....;
}
Switch Statement:
This is an easier implementation to the if-else statements. The keyword "switch" is followed by an expression
that should evaluates to byte, short, char or int primitive data types ,only. In a switch block there can be one
or more labeled cases. The expression that creates labels for the case must be unique. The switch expression
is matched with each case label. Only the matched case is executed ,if no case matches then the default
statement (if present) is executed.
Syntax:
switch(control_expression){ case
expression 1: <statement>; case
expression 2: <statement>;
...
... case expression n:
<statement>; default:
<statement>;
}//end switch
Write a program in JAVA to find the greatest number among three given numbers. Your program should take input from the user
Answer.
import java.io.*;
class GreatestNumber
{
public static void main(String args[]) throws java.lang.Exception
{
int n1,n2,n3;
BufferedReader buffer = new BufferedReader (new InputStreamReader(System.in));
System.out.println("Enter First number");
n1=Integer.parseInt(buffer.readLine());
System.out.println("Enter Second number");
n2=Integer.parseInt(buffer.readLine());
System.out.println("Enter Third number");
n3=Integer.parseInt(buffer.readLine());
if(n1>n2)
{
if(n1>n3)
{
System.out.println("n1 = "+n1+" is greater");
}
else
{
System.out.println("n3 = "+n3+" is greater");
}
}
else
{
if(n2>n3)
{
System.out.println("n2 = "+n2+" is greater");
}
else
{
System.out.println("n3 = "+n3+" is greater");
}
}
}
}
sos
Q . Write features of JAVA programming language in details. What do you understand by bytecode? Also write working of JVM.
Answer.
Java is a general-purpose, high-level programming language. The features of Java:
• Java program is both compiled and interpreted.
• Write once, run anywhere
Java is a software-only platform running on top of other, hardware-based platforms.
• Java Virtual Machine (Java VM)
• The Java Application Programming Interface
(JAVA API)
Features of Java
(1) Simple: It fixes some clumsy features of C++. There is no use of pointers. Java has Automatic garbage
collection. It has rich pre-defined class library http://java.sun.com/j2se/1.4.2/docs/api/
(2) Object oriented: Focus on the data (objects) and methods manipulating the data. All functions are associated with objects. Almost all datatypes are objects (files, strings, etc.). it has potentially better code organization and reuse.
(3) Interpreted: Java compiler generate byte-codes, not native machine code. This compiled byte-codes are platform-independent. Java bytecodes are translated on the fly to machine readable instructions in runtime (Java Virtual Machine).
(4) Portable: Same application runs on all platforms. The sizes of the primitive data types are always the same. The libraries define portable interfaces
(5) Reliable: There is extensive compile-time and runtime error checking. No pointers but real arrays. Memory corruptions or unauthorized memory accesses are impossible. Automatic garbage collection tracks objects usage over time.
(6) Secure: Its usage in networked environments requires more security. Memory allocation model is a major defense. Here access restrictions are forced (private, public).
(7) Multi-threaded: Multiple concurrent threads of executions can run simultaneously. It utilizes a
sophisticated set of synchronization primitives (based on monitors and condition variables paradigm) to achieve this
(8) Dynamic: Java is designed to adapt to evolving environment. Libraries can freely add new methods and instance variables without any effect on their clients. Interfaces promote flexibility and reusability in code by specifying a set of methods an object can perform, but leaves open how these methods should be implemented. It can check the class type in runtime.
ByteCode
Java compilation produces “bytecode” which is an Intermediate code readable by the VM and transferable across the Internet as applets. VM interprets BC into instructions. ByteCode produced on any platform may be executed on any other platform which supports a VM.
JVM
Acts as an interpreter for the bytecode, which takes the bytecodes as input and executes as if it was a physical process executing machine code. JVM is a component of the Java system that interprets and executes the instructions in our class files. Each instance of the JVM has one method area, one heap, and one or more stacks - one for each thread.
• When JVM loads a class file, it puts its information in the method area
• As the program runs, all objects instantiated are stored in the heap
• The stack area is used to store activation records as a program runs
Java is a general-purpose, high-level programming language. The features of Java:
• Java program is both compiled and interpreted.
• Write once, run anywhere
Java is a software-only platform running on top of other, hardware-based platforms.
• Java Virtual Machine (Java VM)
• The Java Application Programming Interface
(JAVA API)
Features of Java
(1) Simple: It fixes some clumsy features of C++. There is no use of pointers. Java has Automatic garbage
collection. It has rich pre-defined class library http://java.sun.com/j2se/1.4.2/docs/api/
(2) Object oriented: Focus on the data (objects) and methods manipulating the data. All functions are associated with objects. Almost all datatypes are objects (files, strings, etc.). it has potentially better code organization and reuse.
(3) Interpreted: Java compiler generate byte-codes, not native machine code. This compiled byte-codes are platform-independent. Java bytecodes are translated on the fly to machine readable instructions in runtime (Java Virtual Machine).
(4) Portable: Same application runs on all platforms. The sizes of the primitive data types are always the same. The libraries define portable interfaces
(5) Reliable: There is extensive compile-time and runtime error checking. No pointers but real arrays. Memory corruptions or unauthorized memory accesses are impossible. Automatic garbage collection tracks objects usage over time.
(6) Secure: Its usage in networked environments requires more security. Memory allocation model is a major defense. Here access restrictions are forced (private, public).
(7) Multi-threaded: Multiple concurrent threads of executions can run simultaneously. It utilizes a
sophisticated set of synchronization primitives (based on monitors and condition variables paradigm) to achieve this
(8) Dynamic: Java is designed to adapt to evolving environment. Libraries can freely add new methods and instance variables without any effect on their clients. Interfaces promote flexibility and reusability in code by specifying a set of methods an object can perform, but leaves open how these methods should be implemented. It can check the class type in runtime.
ByteCode
Java compilation produces “bytecode” which is an Intermediate code readable by the VM and transferable across the Internet as applets. VM interprets BC into instructions. ByteCode produced on any platform may be executed on any other platform which supports a VM.
JVM
Acts as an interpreter for the bytecode, which takes the bytecodes as input and executes as if it was a physical process executing machine code. JVM is a component of the Java system that interprets and executes the instructions in our class files. Each instance of the JVM has one method area, one heap, and one or more stacks - one for each thread.
• When JVM loads a class file, it puts its information in the method area
• As the program runs, all objects instantiated are stored in the heap
• The stack area is used to store activation records as a program runs
Q . Draw and Explain TCP/IP protocol suite in detail.
Answer
The Internet Protocol suite like many protocol suites can be viewed as a set of layers. Each layer solves a set of problems involving the transmission of data, and provides a well-defined service to the upper layer protocols based on using services from some lower layers. Upper layers are logically closer to the user and deal with more abstract data, relying on lower layer protocols to translate data into forms that can eventually be physically transmitted. The TCP/IP model consists of four layers.
From lowest to highest, these are the Link Layer, the Internet Layer, the Transport Layer, and the Application Layer.
The main differences between the OSI architecture and that of TCP/IP relate to the layers above the transport layer (layer 4) and those at the network layer (layer 3). OSI has both, the session layer and the presentation layer, whereas TCP/IP combines both into an application layer. The requirement for a connectionless protocol also required TCP/IP to combine OSI’s physical layer and data link layer into a network level.
The subnet protocol consists of the IMP-IMP protocol which aims to provide a reliable connection between neighboured IMPs. For Ethernet based networks e.g. LANs (Local Area Network), the data link protocol LLC (Logical Link Control) is equally used in OSI and TCP/IP networks.
The OSI transport layer protocol (TP4) and the internet tranport protocol (TCP) have many similarities but also some remarkable differences. Both protocols are built to provide a reliable connection oriented end-toend transport service on top of an unreliable network service. The network service may loose packets, store them, deliver them in the wrong order or even duplicate packets. Both protocols have to be able to deal with the most severe problems e.g. a subnetwork stores valid packets and sends them at a later date. TP4 and TCP have a connect, transfer and a disconnect phase. The principles of doing this are also quite similar.
TCP/IP Protocol Suite
The Internet Protocol suite (commonly TCP/IP) is the set of communications protocols used for the Internet and other similar networks. It is named from two of the most important protocols in it: the Transmission Control Protocol (TCP) and the Internet Protocol (IP), which were the first two networking protocols defined in this standard. Today's IP networking represents a synthesis of several developments that began to evolve in the 1960s and 1970s, namely the Internet and LANs (Local Area Networks), which, together with the invention of the World Wide Web by Sir Tim Berners-Lee in 1989, have revolutionized computing.The Internet Protocol suite like many protocol suites can be viewed as a set of layers. Each layer solves a set of problems involving the transmission of data, and provides a well-defined service to the upper layer protocols based on using services from some lower layers. Upper layers are logically closer to the user and deal with more abstract data, relying on lower layer protocols to translate data into forms that can eventually be physically transmitted. The TCP/IP model consists of four layers.
From lowest to highest, these are the Link Layer, the Internet Layer, the Transport Layer, and the Application Layer.
The main differences between the OSI architecture and that of TCP/IP relate to the layers above the transport layer (layer 4) and those at the network layer (layer 3). OSI has both, the session layer and the presentation layer, whereas TCP/IP combines both into an application layer. The requirement for a connectionless protocol also required TCP/IP to combine OSI’s physical layer and data link layer into a network level.
1. Physical Layer
The physical layer may be either ethernet, SDH-DCC, or some timeslot of a PDH signal. Either OSI protocols and TCP/IP protocols build on the same physical layer standards, thus there is no difference between OSI and TCP/IP in this aspect.2. Data Link Layer
The purpose of the data link layer is to provide error free data transmission even on noisy links. This is achieved by framing of data and retransmission of every frame until it is acknowledged from the far end, using flow control mechanisms. Error detection is done by means of error detection codes. In the internet world there is no real data link layer protocol, but the subnet protocol which has quite many similarities.The subnet protocol consists of the IMP-IMP protocol which aims to provide a reliable connection between neighboured IMPs. For Ethernet based networks e.g. LANs (Local Area Network), the data link protocol LLC (Logical Link Control) is equally used in OSI and TCP/IP networks.
3. Network Layer
The network layer provides routing capabilities between source and destination system. TCP divides messages in datagrams of up to 64k length. Each datagram consists of a header and a text part. Besides some other information, the header contains the source and the destination address of the datagram. IP routes these datagrams through the network using e.g. the protocol OSPF (Open Shortest Path First) or RIP (Route Information Protocol) for path calculation purposes. The service provided by IP is not reliable. Datagrams may be received in the wrong order or they may even get lost in the network.4. Transport Layer
The transport layer provides a reliable end-to-end connection between source and destination system on top of the network layer. It builds an integral part of the whole OSI layering principle and of the internet protocol.The OSI transport layer protocol (TP4) and the internet tranport protocol (TCP) have many similarities but also some remarkable differences. Both protocols are built to provide a reliable connection oriented end-toend transport service on top of an unreliable network service. The network service may loose packets, store them, deliver them in the wrong order or even duplicate packets. Both protocols have to be able to deal with the most severe problems e.g. a subnetwork stores valid packets and sends them at a later date. TP4 and TCP have a connect, transfer and a disconnect phase. The principles of doing this are also quite similar.
Q 1. What do you understand by Internet? Explain concept of IP address in detail.
Answer.
The Internet is a worldwide system of computer networks - a network of networks in which users at any one
computer can, if they have permission, get information from any other computer (and sometimes talk directly
to users at other computers). It was conceived by the Advanced Research Projects Agency (ARPA) of the U.S.
government in 1969 and was first known as the ARPANET. The original aim was to create a network that
would allow users of a research computer at one university to be able to "talk to" research computers at other
universities. A side benefit of ARPANet's design was that, because messages could be routed or rerouted in
more than one direction, the network could continue to function even if parts of it were destroyed in the event
of a military attack or other disaster.
Today, the Internet is a public, cooperative, and self-sustaining facility accessible to hundreds of millions of
people worldwide. Physically, the Internet uses a portion of the total resources of the currently existing public
telecommunication networks. Technically, what distinguishes the Internet is its use of a set of protocols called
TCP/IP (for Transmission Control Protocol/Internet Protocol). Two recent adaptations of Internet technology,
the intranet and the extranet, also make use of the TCP/IP protocol.
Common methods of home access include dial-up, landline broadband (over coaxial cable, fiber optic or
copper wires), Wi-Fi, satellite and 3G technology cell phones.
An Internet Protocol (IP) address is a numerical identification (logical address) that is assigned to devices participating in a computer network utilizing the Internet Protocol for communication between its nodes. Although IP addresses are stored as binary numbers, they are often displayed in more human-readable notations, such as 192.168.100.1 (for IPv4), and 2001:db8:0:1234:0:567:1:1 (for IPv6). The role of the IP address has been characterized as follows: "A name indicates what we seek. An address indicates where it is. A route indicates how to get there." Originally, an IP address was defined as a 32-bit number and this system, now named Internet Protocol Version 4 (IPv4), is still in use today. However, due to the enormous growth of the Internet and the resulting depletion of the address space, a new addressing system (IPv6), using 128 bits for the address, had to be developed. IPv6 is now being deployed across the world; in many places it coexists with the old standard and is transmitted over the same hardware and network links.
The Internet Protocol also is responsible for routing data packets between networks, and IP addresses specify the locations of the source and destination nodes in the topology of the routing system. For this purpose, some of the bits in an IP address are used to designate a sub network. (In CIDR notation, the number of bits used for the subnet follows the IP address. E.g. 192.168.100.1/16) An IP address can be private, for use on a LAN, or public, for use on the Internet or other WAN.
Some of the Web browsers currently available for personal computers include Mozilla Firefox, Safari, Konqueror, Opera, Flock, Internet Explorer, Epiphany and AOL Explorer. Web browsers are the most commonly used type of HTTP user agent. Although browsers are typically used to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or content in file systems.
They work with addresses in following way:
• When we give a name of webpage to open
• The web browser send it to the attached DNS server
• If its lookup table has the corresponding ip, it returns or forward it to the next DNS server
• When browser get corresponding ip for the name provided to try to download the index page or the
mentioned page
• When it gets downloaded then browser interprets the code and displays it.
Internet
The Internet is a worldwide system of computer networks - a network of networks in which users at any one
computer can, if they have permission, get information from any other computer (and sometimes talk directly
to users at other computers). It was conceived by the Advanced Research Projects Agency (ARPA) of the U.S.
government in 1969 and was first known as the ARPANET. The original aim was to create a network that
would allow users of a research computer at one university to be able to "talk to" research computers at other
universities. A side benefit of ARPANet's design was that, because messages could be routed or rerouted in
more than one direction, the network could continue to function even if parts of it were destroyed in the event
of a military attack or other disaster.
Today, the Internet is a public, cooperative, and self-sustaining facility accessible to hundreds of millions of
people worldwide. Physically, the Internet uses a portion of the total resources of the currently existing public
telecommunication networks. Technically, what distinguishes the Internet is its use of a set of protocols called
TCP/IP (for Transmission Control Protocol/Internet Protocol). Two recent adaptations of Internet technology,
the intranet and the extranet, also make use of the TCP/IP protocol.
Common methods of home access include dial-up, landline broadband (over coaxial cable, fiber optic or
copper wires), Wi-Fi, satellite and 3G technology cell phones.
IP Addresses
The Internet Protocol also is responsible for routing data packets between networks, and IP addresses specify the locations of the source and destination nodes in the topology of the routing system. For this purpose, some of the bits in an IP address are used to designate a sub network. (In CIDR notation, the number of bits used for the subnet follows the IP address. E.g. 192.168.100.1/16) An IP address can be private, for use on a LAN, or public, for use on the Internet or other WAN.
Working of web browsers with these addresses.
A web browser is a software application which enables a user to display and interact with text, images, videos, music and other information typically located on a Web page at a website on the World Wide Web or a local area network. Text and images on a Web page can contain hyperlinks to other Web pages at the same or different website. Web browsers allow a user for quick and easy access information provided on many Web pages at many websites by traversing these links.Some of the Web browsers currently available for personal computers include Mozilla Firefox, Safari, Konqueror, Opera, Flock, Internet Explorer, Epiphany and AOL Explorer. Web browsers are the most commonly used type of HTTP user agent. Although browsers are typically used to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or content in file systems.
They work with addresses in following way:
• When we give a name of webpage to open
• The web browser send it to the attached DNS server
• If its lookup table has the corresponding ip, it returns or forward it to the next DNS server
• When browser get corresponding ip for the name provided to try to download the index page or the
mentioned page
• When it gets downloaded then browser interprets the code and displays it.
Thursday, 22 September 2016
Write a program in c to sum ,sub,mult ,division on a one program
#include<stdio.h>
#include<conio.h>
void main()
{
int a,b,sum,sub,mult;
float div;
clrscr();
printf(" enter the value of a and b\n");
scanf("%d%d",&a,&b);
sum=a+b;
sub=a-b;
mult=a*b;
div=a/b;
printf("the sum is =%d",sum);
printf("the sub is =%d",sub);
printf("the mult is =%d",mult);
printf("the div is =%f",div)
getch();
}
#include<conio.h>
void main()
{
int a,b,sum,sub,mult;
float div;
clrscr();
printf(" enter the value of a and b\n");
scanf("%d%d",&a,&b);
sum=a+b;
sub=a-b;
mult=a*b;
div=a/b;
printf("the sum is =%d",sum);
printf("the sub is =%d",sub);
printf("the mult is =%d",mult);
printf("the div is =%f",div)
getch();
}
Saturday, 3 September 2016
How to Prepare A Presentation Profile on Powerpoint
I like to think of Microsoft PowerPoint as a test of basic marketing skills. To create a passing presentation, I need to demonstrate design skills, technical literacy, and a sense of personal style.
If the presentation has a problem (like an unintended font, a broken link, or unreadable text), then I’ve probably failed the test. Even if my spoken presentation is well rehearsed, a bad visual experience can ruin it for the audience. Expertise means nothing without a good presentation to back it up.

If the presentation has a problem (like an unintended font, a broken link, or unreadable text), then I’ve probably failed the test. Even if my spoken presentation is well rehearsed, a bad visual experience can ruin it for the audience. Expertise means nothing without a good presentation to back it up.
PowerPoint Presentation Style Tips
Step 1: Don’t let PowerPoint decide how you use PowerPoint.
Microsoft wanted to provide PowerPoint users with a lot of tools. But this does not mean you should use them all. Here are some key things to look out for:
- Make sure that preset PPT themes complement your needs before you adopt them.
- Try to get away from using Microsoft Office’s default fonts, Calibri and Cambria. Using these two typefaces can make the presentation seem underwhelming.
- Professionals should never use PPT’s action sounds. (Please consider your audience above personal preference).
- PowerPoint makes bulleting automatic, but ask yourself: Are bullets actually appropriate for what you need to do? Sometimes they are, but not always.
- Recent PPT defaults include a small shadow on all shapes. Remove this shadow if it's not actually needed. Also, don’t leave shapes in their default blue.
Step 2: Create custom slide sizes.
While you usually can get away with the default slide size for most presentations, you may need to adjust it for larger presentations on weirdly sized displays. If you need to do that, here's how.
- In the top-left corner, choose "File."
- Select "Page Setup."
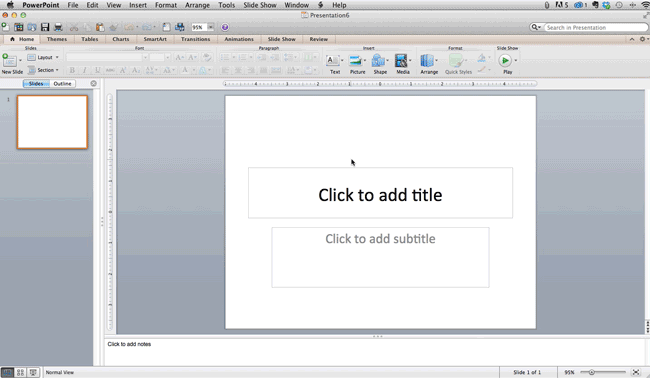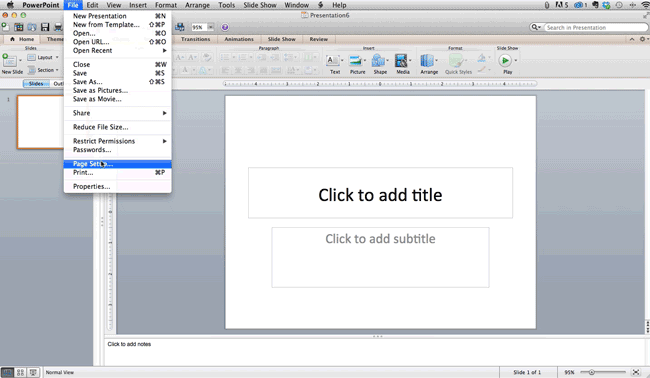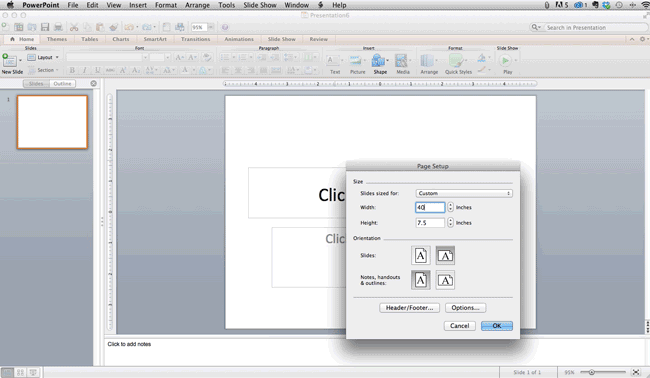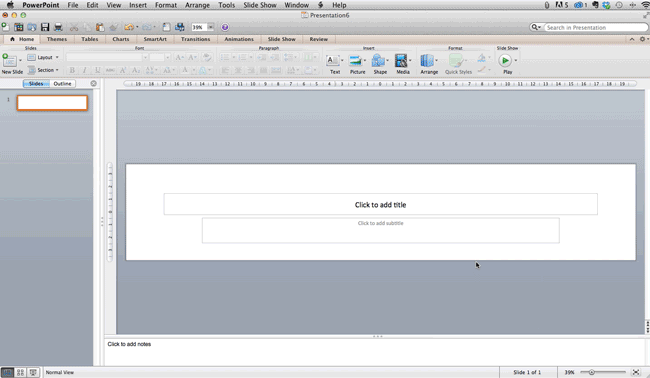
- Type the height and width of the background you'd like, and click "OK."
- A dialogue box will appear. Click "OK" again.
- Your background is resized!
Tip: Resize your slides before you add any objects to them or the dimensions of your objects will become skewed.

Step 3: Edit your slide template design.
Often, it's much easier to edit your PowerPoint template before you start -- this way, you don't have design each slide by hand. Here's how you do that.
- Select "Themes" in the top navigation.
- In the far right, click "Edit Master," then "Slide Master."
- Make any changes you like, then click "Close Master." All current and future slides in that presentation will use that template.\

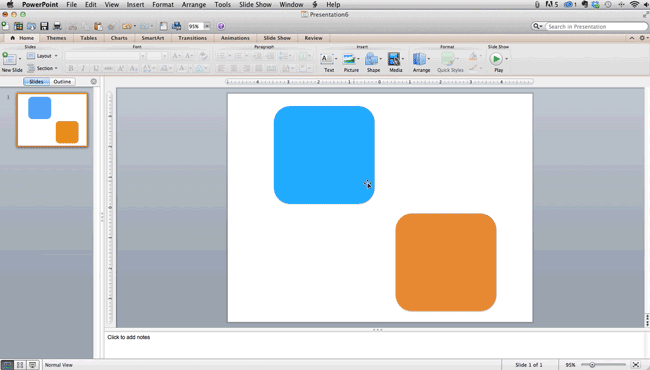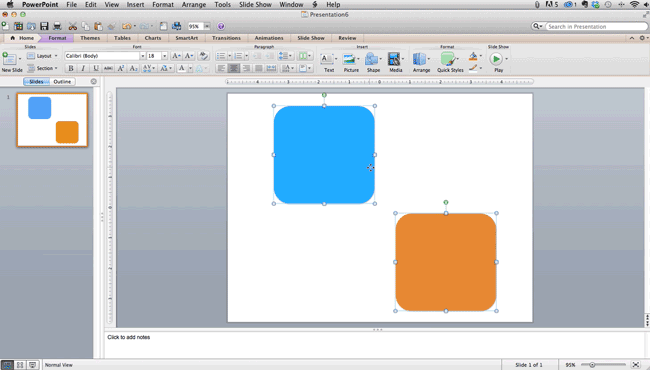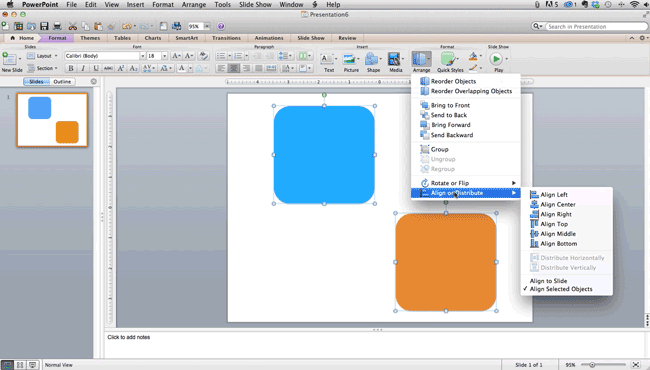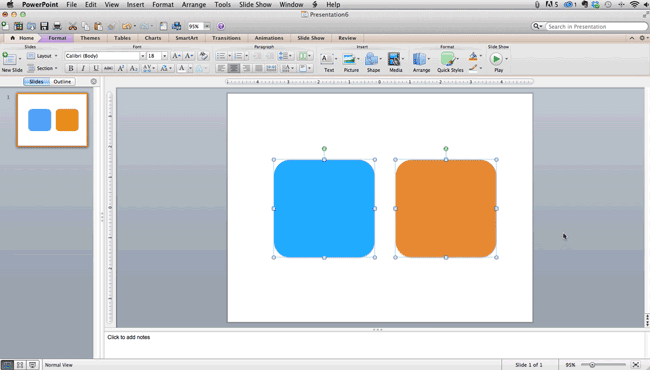
Step 4: Make sure all of your objects are properly aligned.
Having properly aligned objects on your slide is the key to making it look polished and professional. You can manually try to line up your images ... but we all know how that typically works out. You're trying to make sure all of your objects hang out in the middle of your slide, but when you drag them there, it still doesn't look quite right. Get rid of your guessing game and let PowerPoint work its magic with this trick.
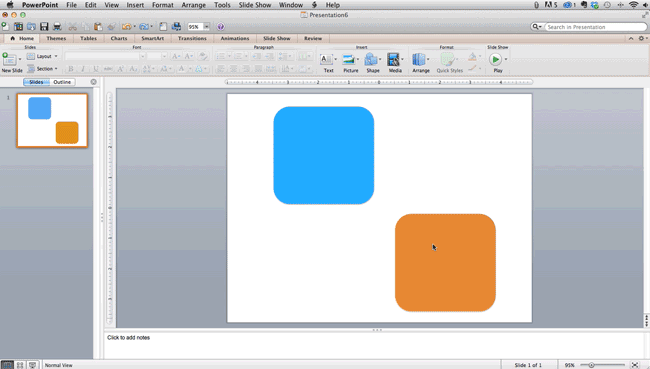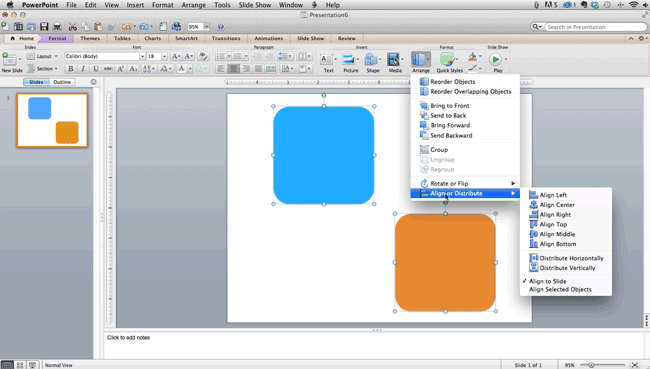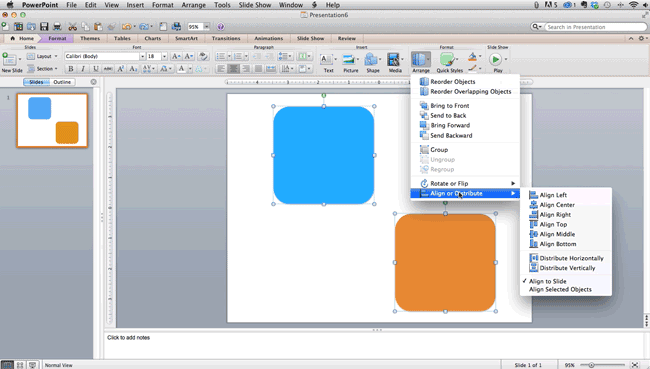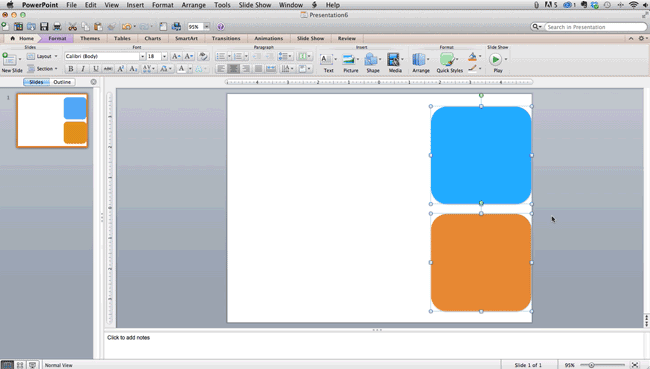
How to align multiple objects:
- Select all objects by holding down "Shift" and clicking on all of them.
- Select "Arrange" in the top options bar, then choose "Align or Distribute."
- Choose the type of alignment you'd like.
How to align objects to the slide:
- Select all objects by holding down "Shift" and clicking on all of them.
- Select "Arrange" in the top options bar, then choose "Align or Distribute."
- Select "Align to Slide."
- Select "Arrange" in the top options bar again, then choose "Align or Distribute."
- Choose the type of alignment you'd like.
 PowerPoint Presentation Design Tips
PowerPoint Presentation Design Tips
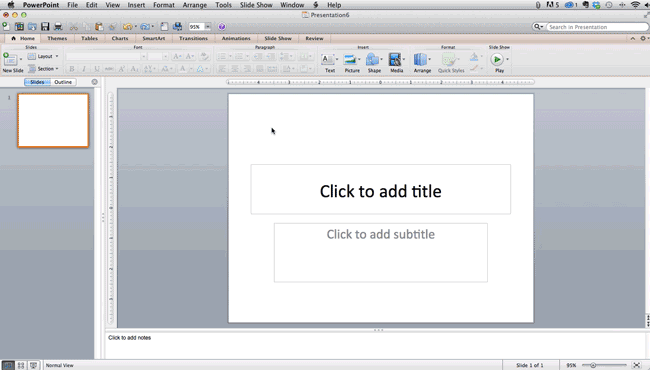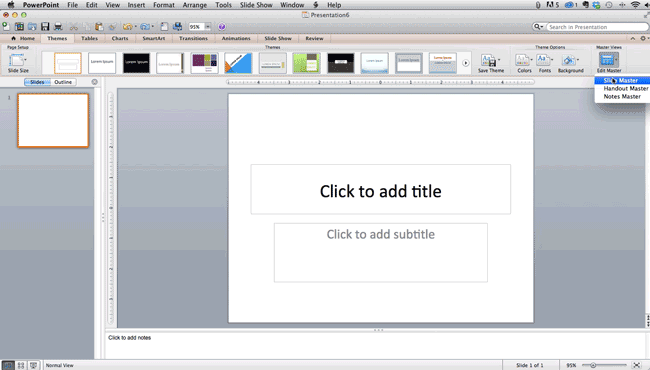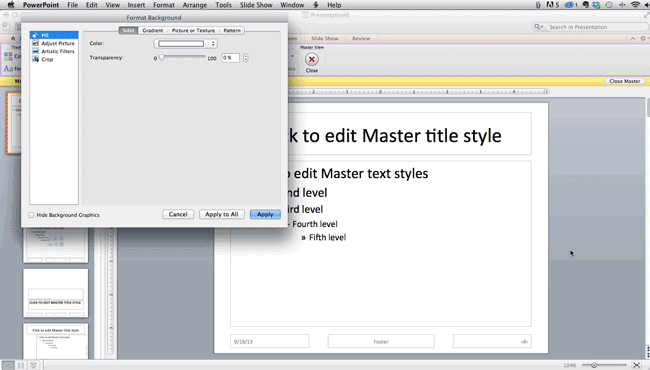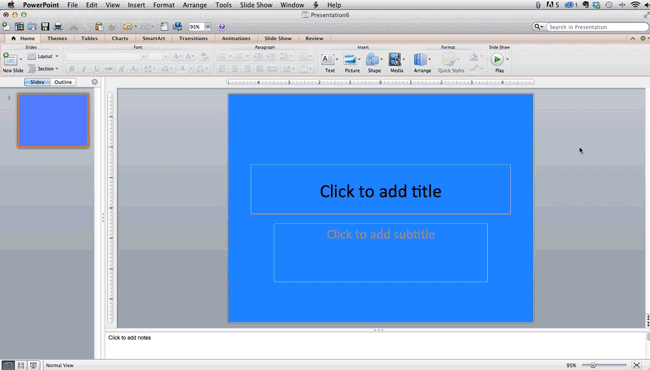
Step 5: Get more control over your objects' designs using "Format" menus.
Format menus allow you to do fine adjustments that otherwise seem impossible. To do this, right click on an object and select the "Format" option. Here, you can fine-tune shadows, adjust shape measurements, create reflections, and much more. The menu that will pop up looks like this: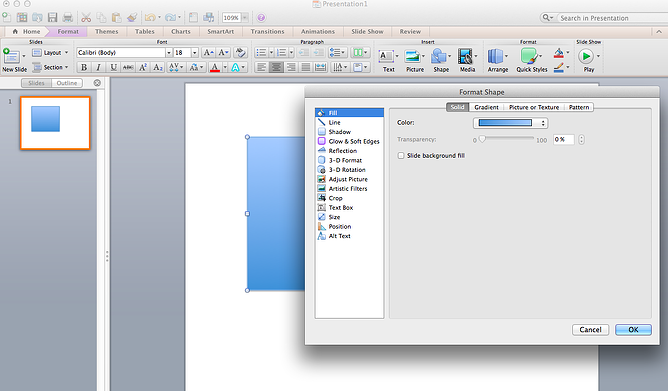 Although the main options can be found on PowerPoint’s format toolbars, look for complete control in the format window menu. Other examples of options available include:
Although the main options can be found on PowerPoint’s format toolbars, look for complete control in the format window menu. Other examples of options available include:
 Although the main options can be found on PowerPoint’s format toolbars, look for complete control in the format window menu. Other examples of options available include:
Although the main options can be found on PowerPoint’s format toolbars, look for complete control in the format window menu. Other examples of options available include:
Adjusting text inside a shape.
Creating a natural perspective shadow behind an object.
Recoloring photos manually and with automatic options.
Step 6: Take advantage of PowerPoint's shapes.
Many users don’t realize how flexible PowerPoint’s shape tools have become. In combination with the expanded format options released by Microsoft in 2010, the potential for good design with shapes is readily available. PowerPoint provides the user with a bunch of great shape options beyond the traditional rectangle, oval, and rounded rectangle patterns, unlike even professional design programs like Adobe Creative Suite or Quark.
Today’s shapes include a highly functional Smart Shapes function, which enables you to create diagrams and flow charts in no time. These tools are especially valuable when you consider that PowerPoint is a visual medium. Paragraphing and bullet lists are boring -- you can use shapes to help express your message more clearly.
Step 7: Create custom shapes.
When you create a shape, right click and press "Edit Points." By editing points, you can create custom shapes that fit your specific need. For instance, you can reshape arrows to fit the dimensions you like.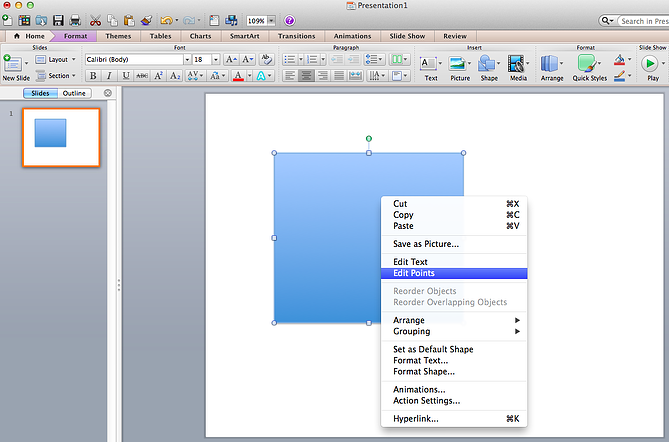 Another option is to combine two shapes together. When selecting two shapes, right-click and go to the "Grouping" sub-menu to see a variety of options.
Another option is to combine two shapes together. When selecting two shapes, right-click and go to the "Grouping" sub-menu to see a variety of options.
 Another option is to combine two shapes together. When selecting two shapes, right-click and go to the "Grouping" sub-menu to see a variety of options.
Another option is to combine two shapes together. When selecting two shapes, right-click and go to the "Grouping" sub-menu to see a variety of options.- Combine creates a custom shape that has overlapping portions of the two previous shapes cut out.
- Union makes one completely merged shape.
- Intersect builds a shape of only the overlapping sections of the two previous shapes.
- Subtract cuts out the overlapping portion of one shape from the other.
- By using these tools rather than trying to edit points precisely, you can create accurately measured custom shapes.
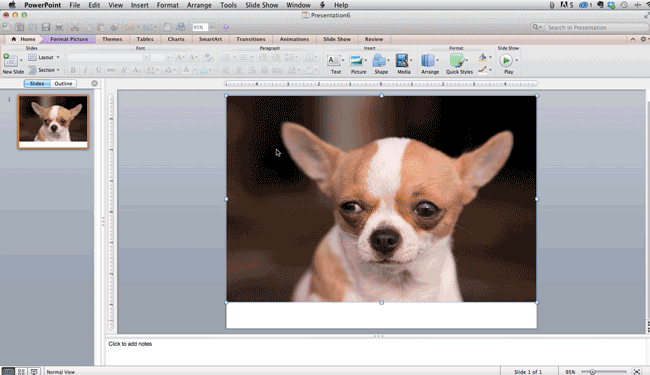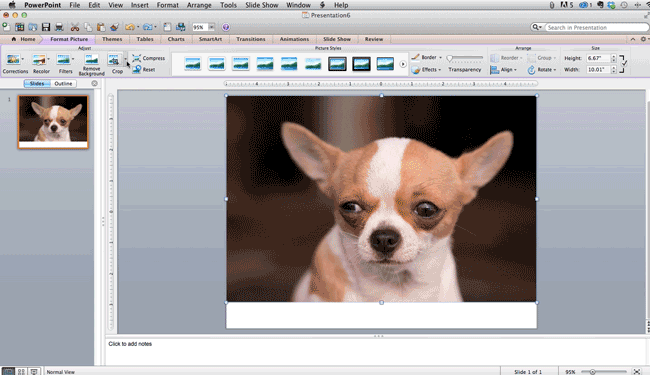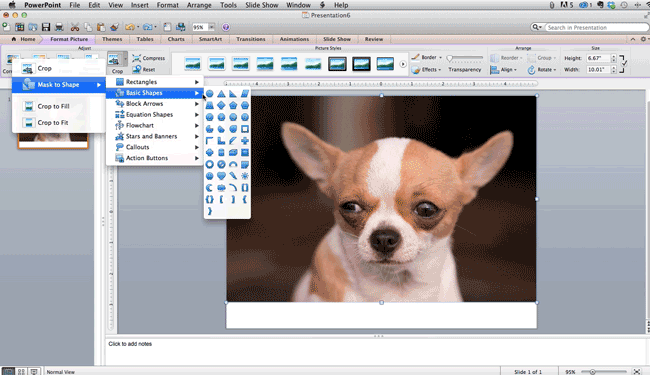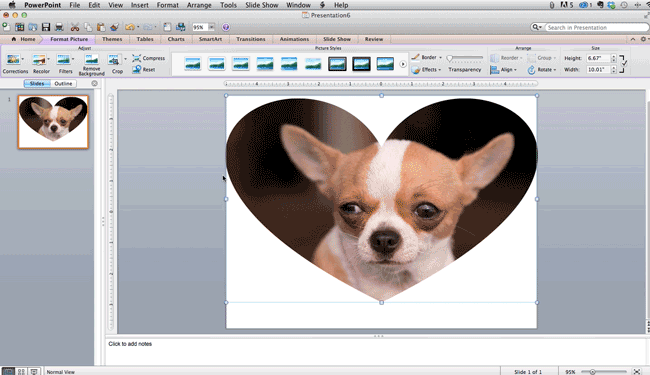
Step 8: Crop images into custom shapes.
Besides creating custom shapes in your presentation, you can also use PowerPoint to crop existing images into new shapes. Here's how you do that:
- Click on the image and select "Format" in the options bar.
- Choose "Crop," then "Mask to Shape," and then choose your desired shape. Ta-da! Custom-shaped photos.
 Step 9: Present websites within PowerPoint.
Step 9: Present websites within PowerPoint.
Tradition says that if you want to show a website in a PowerPoint, you should just create link to the page and prompt a browser to open. For PC users, there’s a better option.
Third party software that integrates fully into PowerPoint’s developer tab can be used to embed a website directly into your PowerPoint using a normal HTML iframe. One of the best tools is LiveWeb, a third-party software developed independently.
By using LiveWeb, you don’t have to interrupt your PowerPoint, and your presentation will remain fluid and natural. Whether you embed a whole webpage or just a YouTube video, this can be a high-quality third party improvement.
Unfortunately, Mac users don’t have a similar option. A good second choice is to take screen shots of the website, link in through a browser, or embed media (such as a YouTube video) by downloading it directly to your computer.
Friday, 2 September 2016
History of Python Language
Python’s early development started at a research institute in Amsterdam called CWI, which is a Dutch acronym for a phrase that translates into English as Centre for Mathematics and Computer Science. CWI is an interesting place; funded by the Dutch government’s Department of Education and other research grants, it conducts academic-level research into computer science and mathematics. At any given time there are plenty of Ph.D. students wandering about and old-timers in the profession may still remember its original name, the Mathematical Centre. Under this name, it was perhaps most famous for the invention of Algol 68.
I started working at CWI in late 1982, fresh out of university, as a programmer in the ABC group led by Lambert Meertens and Steven Pemberton. After 4 or 5 years the ABC project was terminated due to the lack of obvious success and I moved to CWI’s Amoeba group led by Sape Mullender. Amoeba was a micro-kernel-based distributed system being jointly developed by CWI and the Vrije Universiteit of Amsterdam, under leadership of Andrew Tanenbaum. In 1991 Sape left CWI for a professorship at the University of Twente and I ended up in the newly formed CWI multimedia group led by Dick Bulterman.
Python is a direct product of my experience at CWI. As I explain later, ABC gave me the key inspiration for Python, Amoeba the immediate motivation, and the multimedia group fostered its growth. However, so far as I know, no funds at CWI were ever officially earmarked for its development. Instead, it merely evolved as an important tool for use in both the Amoeba and multimedia groups.
My original motivation for creating Python was the perceived need for a higher level language in the Amoeba project. I realized that the development of system administration utilities in C was taking too long. Moreover, doing these in the Bourne shell wouldn’t work for a variety of reasons. The most important one was that as a distributed micro-kernel system with a radically new design, Amoeba’s primitive operations were very different (and finer-grain) than the traditional primitive operations available in the Bourne shell. So there was a need for a language that would “bridge the gap between C and the shell.” For a long time, this was Python’s main catchphrase.
At this point, you might ask "why not port an existing language?" In my view, there weren’t a lot of suitable languages around at that time. I was familiar with Perl 3, but it was even more tied to Unix than the Bourne shell. I also didn’t like Perl’s syntax--my tastes in programming language syntax were strongly influenced by languages like Algol 60, Pascal, Algol 68 (all of which I had learned early on), and last but not least, ABC, on which I’d spent four years of my life. So, I decided to design a language of my own which would borrow everything I liked from ABC while at the same time fixing all its problems (as I perceived them).
The first problem I decided to fix was the name! As it happened, the ABC team had some trouble picking a name for its language. The original name for the language, B, had to be abandoned because of confusion with another language named B, that was older and better known. In any case, B was meant as a working title only (the joke was that B was the name of the variable containing the name of the language--hence the italics). The team had a public contest to come up with a new name, but none of the submissions made the cut, and in the end, the internal back up candidate prevailed. The name was meant to convey the idea that the language made programming “as simple as ABC”, but it never convinced me all that much.
So, rather than over-analyzing the naming problem, I decided to under-analyze it. I picked the first thing that came to mind, which happened to be Monty Python’s Flying Circus, one of my favorite comedy troupes. The reference felt suitably irreverent for what was essentially a “skunkworks project”. The word “Python” was also catchy, a bit edgy, and at the same time, it fit in the tradition of naming languages after famous people, like Pascal, Ada, and Eiffel. The Monty Python team may not be famous for their advancement of science or technology, but they are certainly a geek favorite. It also fit in with a tradition in the CWI Amoeba group to name programs after TV shows.
For many years I resisted attempts to associate the language with snakes. I finally gave up when O’Reilly wanted to put a snake on the front of their first Python book "Programming Python". It was an O’Reilly tradition to use animal pictures, and if it had to be an animal, it might as well be a snake.
With the naming issue settled, I started working on Python in late December 1989, and had a working version in the first months of 1990. I didn’t keep notes, but I remember vividly that the first piece of code I wrote for Python’s implementation was a simple LL(1) parser generator I called “pgen." This parser generator is still part of the Python source distribution and probably the least changed of all the code. This early version of Python was used by a number of people at CWI, mostly, but not exclusively in the Amoeba group during 1990. Key developers besides myself were my officemates, programmers Sjoerd Mullender (Sape’s younger brother) and Jack Jansen (who remained one of the lead developers of the Macintosh port for many years after I left CWI).
On February 20, 1991, I first released Python to the world in the alt.sources newsgroup (as 21 uuencoded parts that had to be joined together and uudecoded to form a compressed tar file). This version was labeled 0.9.0, and released under a license that was an almost verbatim copy of the MIT license used by the X11 project at the time, substituting “Stichting Mathematisch Centrum”, CWI’s parent organization, as the responsible legal entity. So, like almost everything I’ve written, Python was open source before the term was even invented by Eric Raymond and Bruce Perens in late 1997.
There was immediately a lot of feedback and with this encouragement I kept a steady stream of releases coming for the next few years. I started to use CVS to track changes and to allow easier sharing of coding responsibilities with Sjoerd and Jack (Coincidentally, CVS was originally developed as a set of shell scripts by Dick Grune, who was an early member of the ABC group). I wrote a FAQ, which was regularly posted to some newsgroup, as was customary for FAQs in those days before the web, started a mailing list, and in March 1993 the comp.lang.python newsgroup was created with my encouragement but without my direct involvement. The newsgroup and mailing list were joined via a bidirectional gateway that still exists, although it is now implemented as a feature of mailman – the dominant open source mailing list manager, itself written in Python.
In the summer of 1994, the newsgroup was buzzing with a thread titled “If Guido was hit by a bus?” about the dependency of the growing Python community on my personal contributions. This culminated in an invitation from Michael McLay for me to spend two months as a guest researcher at NIST, the US National Institute for Standards and Technology, formerly the National Bureau of Standards, in Gaithersburg, Maryland. Michael had a number of “customers” at NIST who were interested in using Python for a variety of standards-related projects and the budget for my stay there was motivated by the need to help them improve their Python skills, as well as possibly improving Python for their needs.

I started working at CWI in late 1982, fresh out of university, as a programmer in the ABC group led by Lambert Meertens and Steven Pemberton. After 4 or 5 years the ABC project was terminated due to the lack of obvious success and I moved to CWI’s Amoeba group led by Sape Mullender. Amoeba was a micro-kernel-based distributed system being jointly developed by CWI and the Vrije Universiteit of Amsterdam, under leadership of Andrew Tanenbaum. In 1991 Sape left CWI for a professorship at the University of Twente and I ended up in the newly formed CWI multimedia group led by Dick Bulterman.
Python is a direct product of my experience at CWI. As I explain later, ABC gave me the key inspiration for Python, Amoeba the immediate motivation, and the multimedia group fostered its growth. However, so far as I know, no funds at CWI were ever officially earmarked for its development. Instead, it merely evolved as an important tool for use in both the Amoeba and multimedia groups.
My original motivation for creating Python was the perceived need for a higher level language in the Amoeba project. I realized that the development of system administration utilities in C was taking too long. Moreover, doing these in the Bourne shell wouldn’t work for a variety of reasons. The most important one was that as a distributed micro-kernel system with a radically new design, Amoeba’s primitive operations were very different (and finer-grain) than the traditional primitive operations available in the Bourne shell. So there was a need for a language that would “bridge the gap between C and the shell.” For a long time, this was Python’s main catchphrase.
At this point, you might ask "why not port an existing language?" In my view, there weren’t a lot of suitable languages around at that time. I was familiar with Perl 3, but it was even more tied to Unix than the Bourne shell. I also didn’t like Perl’s syntax--my tastes in programming language syntax were strongly influenced by languages like Algol 60, Pascal, Algol 68 (all of which I had learned early on), and last but not least, ABC, on which I’d spent four years of my life. So, I decided to design a language of my own which would borrow everything I liked from ABC while at the same time fixing all its problems (as I perceived them).
The first problem I decided to fix was the name! As it happened, the ABC team had some trouble picking a name for its language. The original name for the language, B, had to be abandoned because of confusion with another language named B, that was older and better known. In any case, B was meant as a working title only (the joke was that B was the name of the variable containing the name of the language--hence the italics). The team had a public contest to come up with a new name, but none of the submissions made the cut, and in the end, the internal back up candidate prevailed. The name was meant to convey the idea that the language made programming “as simple as ABC”, but it never convinced me all that much.
So, rather than over-analyzing the naming problem, I decided to under-analyze it. I picked the first thing that came to mind, which happened to be Monty Python’s Flying Circus, one of my favorite comedy troupes. The reference felt suitably irreverent for what was essentially a “skunkworks project”. The word “Python” was also catchy, a bit edgy, and at the same time, it fit in the tradition of naming languages after famous people, like Pascal, Ada, and Eiffel. The Monty Python team may not be famous for their advancement of science or technology, but they are certainly a geek favorite. It also fit in with a tradition in the CWI Amoeba group to name programs after TV shows.
For many years I resisted attempts to associate the language with snakes. I finally gave up when O’Reilly wanted to put a snake on the front of their first Python book "Programming Python". It was an O’Reilly tradition to use animal pictures, and if it had to be an animal, it might as well be a snake.
With the naming issue settled, I started working on Python in late December 1989, and had a working version in the first months of 1990. I didn’t keep notes, but I remember vividly that the first piece of code I wrote for Python’s implementation was a simple LL(1) parser generator I called “pgen." This parser generator is still part of the Python source distribution and probably the least changed of all the code. This early version of Python was used by a number of people at CWI, mostly, but not exclusively in the Amoeba group during 1990. Key developers besides myself were my officemates, programmers Sjoerd Mullender (Sape’s younger brother) and Jack Jansen (who remained one of the lead developers of the Macintosh port for many years after I left CWI).
On February 20, 1991, I first released Python to the world in the alt.sources newsgroup (as 21 uuencoded parts that had to be joined together and uudecoded to form a compressed tar file). This version was labeled 0.9.0, and released under a license that was an almost verbatim copy of the MIT license used by the X11 project at the time, substituting “Stichting Mathematisch Centrum”, CWI’s parent organization, as the responsible legal entity. So, like almost everything I’ve written, Python was open source before the term was even invented by Eric Raymond and Bruce Perens in late 1997.
There was immediately a lot of feedback and with this encouragement I kept a steady stream of releases coming for the next few years. I started to use CVS to track changes and to allow easier sharing of coding responsibilities with Sjoerd and Jack (Coincidentally, CVS was originally developed as a set of shell scripts by Dick Grune, who was an early member of the ABC group). I wrote a FAQ, which was regularly posted to some newsgroup, as was customary for FAQs in those days before the web, started a mailing list, and in March 1993 the comp.lang.python newsgroup was created with my encouragement but without my direct involvement. The newsgroup and mailing list were joined via a bidirectional gateway that still exists, although it is now implemented as a feature of mailman – the dominant open source mailing list manager, itself written in Python.
In the summer of 1994, the newsgroup was buzzing with a thread titled “If Guido was hit by a bus?” about the dependency of the growing Python community on my personal contributions. This culminated in an invitation from Michael McLay for me to spend two months as a guest researcher at NIST, the US National Institute for Standards and Technology, formerly the National Bureau of Standards, in Gaithersburg, Maryland. Michael had a number of “customers” at NIST who were interested in using Python for a variety of standards-related projects and the budget for my stay there was motivated by the need to help them improve their Python skills, as well as possibly improving Python for their needs.
Characterstic Of Python
- Generator Expressions
- input() Let me explain, I have not seen a language (so far), where you can assign a value to a statement that prints something, it is like ruby's print/gets, but with a value assigned to the print, instead of: print "Foo" bar = gets
- yield
- Many types of datasets: ordereddict, namedtuple, array, list, tuple, dictionary
Wednesday, 31 August 2016
How to save your money 8 tips.
1. Record your expenses
2. Make a budget
3. Plan on saving money
4. Set savings goals
Setting savings goals makes it much easier to get started. Begin by deciding how long it will take to reach each goal. Some short-term goals (which can usually take 1-3 years) include:Starting an emergency fund to cover 6 months to a year of living expenses (in case of job loss or other emergencies)
Saving money for a vacation
Saving to buy a new car
Saving to pay taxes (if they are not already deducted by your employer)
Try the Bank of America savings goal calculator to see how long it will take for you to reach your saving goal.
Long-term savings goals are often several years or even decades away and can include:
Saving for retirement
Putting money away for your child's college education
Saving for a down payment on a house or to remodel your current home
5. Decide on your priorities
Different people have different priorities when it comes to saving money, so it makes sense to decide which savings goals are most important to you. Part of this process is deciding how long you can wait to save up for a goal and how much you want to put away each month to help you reach it. As you do this for all your goals, order them by priority and set money aside accordingly in your monthly budget. Remember that setting priorities means making choices. If you want to focus on saving for retirement, some other goals might have to take a back seat while you make sure you're hitting your top targets.6. Different savings and investment strategies for different goals
If you're saving for short-term goals, consider using these FDIC-insured deposits accounts:A regular savings account, which is easily accessible
A high-yield savings account, which often has a higher interest rate than a standard savings account
A bank money market savings account, which has a variable interest rate that could increase as your savings grow
A CD (certificate of deposit), which locks in your money at a specific interest rate for a specific period of time
For long-term goals consider:
FDIC-insured IRAs, which are built for purposes such as retirement savings. If you’re not sure how much money you should set aside for retirement, give the Merrill Edge retirement calculator a try.
Securities, like stocks and mutual funds. These investment products are available through investment accounts with a broker-dealer (e.g. Merrill Edge). Remember that securities, such as stocks and mutual funds, are not insured by the FDIC, are not deposits or other obligations of a bank and are not guaranteed by a bank, and are subject to investment risks including the possible loss of principal invested.
7. Make saving money easier with automatic transfers
Automatic transfers to your savings account can make saving money much easier. By moving money out of your checking account, you'll be less likely to spend money you wanted to use for savings. There are many options for setting up transfers. You choose how often you want to transfer money and which accounts you want to use for the transfers. You can even split your direct deposit between your checking and savings accounts to contribute to your savings with each paycheck. Thinking of saving as a regular expense is a great way to keep on target with your savings goals.8. Watch your savings grow
Check your progress every month. Not only will this help you stick to your personal savings plan, but it also helps you identify and fix problems quickly. With these simple ways to save money, it may even inspire you to save more and hit your goals faster.Tuesday, 30 August 2016
how to improve your personality.
In order to help all spiritual seekers who wish to make fast spiritual progress we developed these intensive spiritual workshops to provide clear practical guidance and a highly conducive environment for spiritual growth.
If you have desire to know yourself at a much deeper level, to nurture divine qualities and greatly increase the pace of your inner change then we encourage you to take the benefit of this unique opportunity.
The workshops include interactive and practical sessions to help you:
If you incorporate the simple steps of spiritual practice that you will learn in this workshop, you will benefit from greater spiritual protection, peace of mind and experience fast spiritual development.
The workshop groups are kept small with around 10 attendees only, so that we can give you individual support for your spiritual practice taking into account your personality, state of mind and spiritual path. We will also provide you with all the necessary tools to further your Spiritual journey once you are back home.
If you want to see the video click here on video
If you have desire to know yourself at a much deeper level, to nurture divine qualities and greatly increase the pace of your inner change then we encourage you to take the benefit of this unique opportunity.
The workshops include interactive and practical sessions to help you:
- Overcome personality defects and reduce ego
- Gain higher levels of protection from spiritual distress and learn about various self-healing methods
- Learn how the spiritual dimension can affect our lives
- Acquire tools and guidance to go to the next level of spiritual practice
If you incorporate the simple steps of spiritual practice that you will learn in this workshop, you will benefit from greater spiritual protection, peace of mind and experience fast spiritual development.
The workshop groups are kept small with around 10 attendees only, so that we can give you individual support for your spiritual practice taking into account your personality, state of mind and spiritual path. We will also provide you with all the necessary tools to further your Spiritual journey once you are back home.
If you want to see the video click here on video
WHO IS HACKER
Hacker is a term used by some to mean "a clever programmer" and by others, especially those in popular media, to mean "someone who tries to break into computer systems."
1) Eric Raymond, compiler of The New Hacker's Dictionary, defines a hacker as a clever programmer. A "good hack" is a clever solution to a programming problem and "hacking" is the act of doing it. Raymond lists five possible characteristics that qualify one as a hacker, which we paraphrase here:
A person who enjoys learning details of a programming language or system
A person who enjoys actually doing the programming rather than just theorizing about it
A person capable of appreciating someone else's hacking
A person who picks up programming quickly
A person who is an expert at a particular programming language or system, as in "UNIX hacker"
Raymond deprecates the use of this term for someone who attempts to crack someone else's system or otherwise uses programming or expert knowledge to act maliciously. He prefers the term cracker for this meaning.
2) The term hacker is used in popular media to describe someone who attempts to break into computer systems. Typically, this kind of hacker would be a proficient programmer or engineer with sufficient technical knowledge to understand the weak points in a security system. For more on this usage, see cracker.
In other word
"1.a person who uses computers to gain unauthorized access to data.
2.a person or thing that hacks or cuts roughly."
Friday, 26 August 2016
how to trace a location
You can see the location of your mobile phone on google
click here on mobile tracer and then you enter your no and see the location online on our website
mytrickycoding
Subscribe to:
Comments (Atom)













